Latest Cloud Security Management: Technology is advancing, therefore we must adapt the way we secure data to today’s needs and the future. You will agree that working from home has increased significantly during the COVID 19 pandemic. This is forcing companies and their employees to rely more on virtual private networks (VPNs). They now work with their security operations center (SOC) colleagues remotely and give more attention to data protection. Security Management: Why Companies Need a Unified Cloud Platform.
Notice that the global Corona Virus pandemic has sped up emerging trends in IT and cybersecurity. These trends includes digital adoption and noisy tools and agility within the SOC, to name a few. Now, to keep up with the trend, companies can leverage a central security management platform approach to adapt and modernize their SOCs (security operations center).
Considerations for Security Management
First, you should consider the ‘incident’ side of protecting data. The idea is clear: an improvement to any individual aspect of incident response makes the process more efficient overall. Take for instance, the faster the team spots a breach, the faster they can resolve it the problem.
Notwithstanding, threat detection is usually noisy. To be able to streamline the events to a more accurate narrative and also discover the root cause is vital. Additionally, locating where the threat actor has entered the network. More importantly, where he or she has gone or is going becomes key for fixing the breach.
After all, the art of remediation isn’t just only to throw patches at the breach problem. It also involves finding which assets must be protected first. Also, discovering which paths to and from the network are the mostly exposed to the threat.
What Parts of the System Are Mostly at Risk?
Risk includes the following components:
- First and foremost, the Internet-facing devices are much more at risk than on-premises machines and assets. Having good insight into a web server is more important than protecting a print server.
- Secondly, Exposure matters. Keep in mind that a file type that can be edited, destroyed or altered is more at risk than a file that can simply be observed by a threat actor (although, this is not a great outcome either).
- Thirdly, if files leave the network, the security operations team must prevent the leakage.
- Lastly, the cloud platform should be able to determine if users have access to specific data.
Note that the concept of a network itself is changing. Maybe a century ago, security teams could stash critical assets behind an on-premises firewall, and the network architecture was flat. Remember that this is no longer the case. The network comprises of private and public clouds (usually more than one public cloud).
Of course, workloads exist in containers, mobile users and Internet of things (IoT) devices. Computer Networks are becoming more complex, but the people protecting them still have the same aims. Therefore, a modern approach can provide more streamlined management and workflows across a more complex landscape.
Security Management Takes A Strong Platform
Note that a state-of-the-art cybersecurity platform must be cloud native but not confined to software as a service (SaaS). Thus, the platform should be flexible enough to deploy where the owner wants it. It can be on premises, in a public or private cloud. It can even be as a hybrid architecture.
Cloud allows for cloud compute, a central vantage point for search, multi-tenancy, remote storage and better north-south ingress/egress. In addition, the possibility of using public cloud infrastructure as a service (IaaS) to connect multiple appliances. A flexible architecture also supports groups with hybrid environments, including multiple clouds and on-premises solutions.
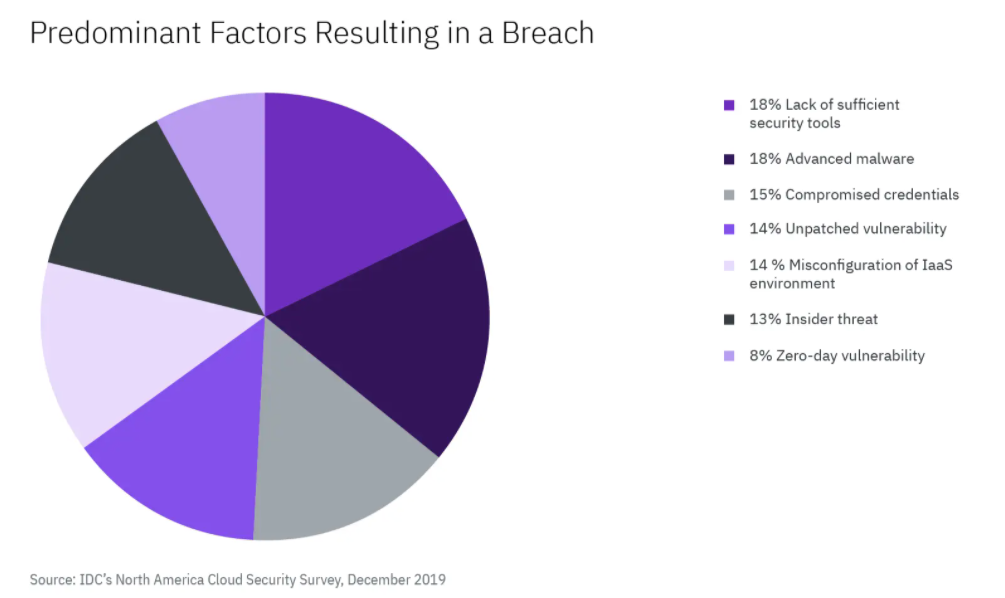
Brand new tools and the shift to remote work mean the field changes fast. IaaS insight is not so much a suggested good practice as it is a requisite cost of doing business. International Data Corporation (IDC’s) December 2019 North America Cloud Security Survey asked respondents to identify the source of the most recent breach in their IaaS environments. Results came in, and this is the chart below illustrates their responses.
Causes of the Most Recent Breach in an IaaS Environment
Q: For your most recent breach of an IaaS environment, what was the predominant factor that resulted in the breach?
You can protect on-premises servers with a stateful firewall and air-gapping machines. Or, simply configuring servers and routers without internet access as on-premises security measures. Companies may not wish to relinquish on-premises security because different applications and computers were designed for legacy architectures and would be (or, are proving to be) difficult to replicate in the cloud.
Elements of a Good Security Management Platform
First and foremost, the platform must be vendor agnostic. This seems like a tough pill to swallow for any product vendor. Moreover, vendors must seek the best outcomes for their clients. End users cannot be cowed into vendor lock. Also, a key feature for any tool or platform is that the business is not required to ‘rip and replace’ existing tools. Read out blog on How to choose a Reliable Vendor.
Next, the platform should also include data loss statistics and file integrity management. To be fair, several tools defend data from improper access or obfuscation. However, being able to see whether data is leaving a network should be a line item.
Bottomline, a good platform should manage and verify the quality of alerts within the platform even before the analyst considers looking into it. Also, a smart platform should be the central nervous system of data coming to and from firewalls, threat intelligence tools, other software like SIEM tools, endpoints etc.
Managing False Alarms
Do not forget that tools aren’t all you need in this. The tools often flag changes that are based on normal network conditions (e.g., new configurations, operating system and software upgrades, etc.). A platform really needs to weed out weak signals and correlate stronger alerts.
Furthermore, the platform will ensure to connect the process of incident response directly to workflow. For example, when an analyst researches a specific malware family, the dashboard should prompt what is known about the malware type. Going forward, this action is not suppose to require more mouse clicks. Good Playbooks are very helpful to analysts, too. This helps in prompting what to do next and where to start fixing problems. After all, today, everything that makes the work a little more efficient counts.
You can learn more from our recent blog, Modernizing Your Security Operations Center for the Cloud. Also, find and view the on-demand webinar; How to Effectively Modernize your SOC, (from YouTube) to learn more about effectively modernizing your SOC and hear from a panel of IBM Security experts. Read more from the topics below;
- Some Hybrid Cloud Security Risks Challenges and How to Repair them
- Public Cloud Security Challenges and Solutions – Tools & Tutorials
- Cloud Security: Best Practices to Secure Your Hybrid Cloud Infrastructure
- Cyber Security Predictions for Today, Tech protection & Intelligence Report
- Importance of Web App Security over the Increasing Web Application Attacks
- Future Cyber Security Predictions & Protection for Next Year
For the full story on unified, cloud-native security management platforms and how IBM Cloud Pak for Security can help organizations achieve efficient and effective security, download the IDC paper, “Making Molehills from Mountains: Using a Platform Approach to Simplify Security Management and Operations,” which was sponsored by IBM company.







