How to Detect and Prevent DNS Cache Poisoning. But first, let me ask this; How do Hackers Spoof DNS Requests With DNS Cache Poisoning? We are going to look at this problems ad solution of DNS spoofing and cybercrime. Read on.
What is DNS (Domain Name Server)?
Domain Name Server (DNS) Spoofing is a cyber attack that trick. Spoofing the Domain Name Server (DNS) is a cyber attack that tricks your machine into believing it’s going to the right website, but it’s not. DNS cache poisoning is used by attackers to hijack internet traffic and steal user credentials or personal data.
DNS cache poisoning and DNS spoofing are interchangeably interchangeable and frequently used. But, you can think of them, to be exact, as the how and what of the same cyber attack. The hacker wants users to be fooled into accessing insecure websites with their private data. How’re they going to do this? By making the DNS cache poisoned.
What they do is spoof or replace a specific website with the DNS data so that it redirects to the server of the hacker and not the actual web server. From there, the hacker is prepared to execute a phishing attack, steal information, or even inject malware into the system of the victim.
What is DNS Spoofing and Cache Poisoning?
We need a refresher on what DNS and DNS caching is before we address the attack by the hackers. DNS is the catalog for IP addresses and domain names worldwide. Think of it as an Internet phonebook. This converts end-user-friendly URLs such as Varonis.com to an IP address such as 192.168.1.169 used by networking computers.
The mechanism that stores these addresses in DNS servers all over the world is DNS caching. The original developers developed a distributed DNS system to keep your DNS requests fast. A list of DNS records it knows is stored by each server-this is called a cache.
If the IP address you need is not identified by your nearest DNS server, it asks other upstream DNS servers before the IP address for the website you are trying to reach is located. Your DNS server then saves the new entry for quicker response times to your cache.
Examples and Effects of DNS Cache Poisoning
DNS has not been planned at all to handle the modern internet. Over the years, it has gotten better, but one misconfigured DNS server that pulled DNS entries from a server in China-and no one can instantly get to Facebook. This incident highlights how reliant we are on DNS. A server is misconfigured by one person, and immediately hundreds of millions of individuals feel the consequences.
The attackers who used a DNS cache poisoning attack to hijack traffic to their own WikiLeaks-like version were also targeting WikiLeaks. This was an intentional attack planned with some success to hold traffic away from WikiLeaks.
For ordinary individuals, DNS cache poisoning attacks are sly and hard to detect. DNS is a trust first device at the moment, which is why it’s quick to take advantage of. Humans trust a fault in DNS, and never really check if the address in their browser is the address they were expecting. To steal credentials or more, attackers take advantage of this complacency and inattentiveness.
How Does a DNS Cache Poisoning Attack Work?
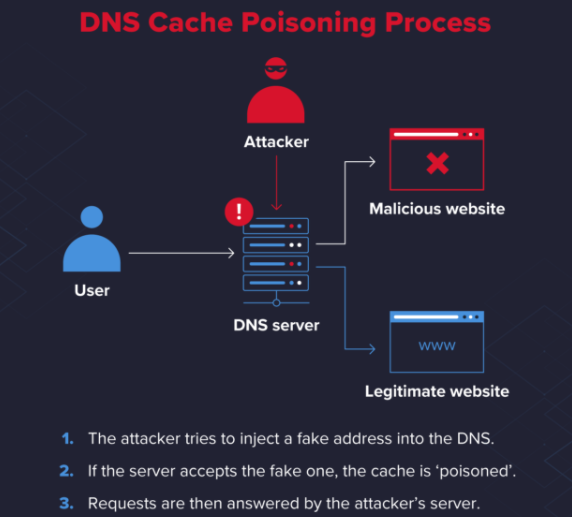
DNS cache poisoning is when there is an entry on your nearest DNS server that sends you to the wrong address, normally one that is managed by an attacker. Here are a few different approaches that are used by attackers to poison the DNS cache.
Hijacking the Local Network With ARP Spoofing
The local network can be a target that is unexpectedly vulnerable. Most managers would assume that they have this locked down, but the devil may be in the specifics. Work-from-home workers are one common problem. Is their Wi-Fi protected? In just a couple of hours, hackers will break a weak Wi-Fi password. Another one is revealing open ethernet ports in hallways and public lobbies.
Let’s take a look at how, in one of those cases, a hacker might possibly use access to the local network.
The hacker will first create a phishing page that they can use to obtain user credentials and other useful information. Locally on the network or remotely on a server with a single python code line, they could then host this site.
The hacker could then begin monitoring the network from there with software such as Betterrcap. They are mapping and exploring the target network at this point, but traffic still flows through the router.
How Does Hackers Attack Your DNS?
Next, to restructure the network internally, the hacker will use ARP spoofing. Devices on a network use ARP, or address resolution protocol, to connect a device’s MAC address with an IP address on the network. Bettercap would send out ARP messages telling all the network devices that the router is the hacker’s machine.
The hacker will run Bettercap’s DNS spoofing module once all traffic is re-routed through the hacker’s device. This will search for a targeted domain for any requests and send a false response back to the victim. The fake request contains the hacker’s computer’s IP address, redirecting any request to the target website to the hacker’s hosted phishing page.
The hacker will now see traffic intended for other network devices and redirect requests to any website. On this tab, the hacker will see all the victim does, such as gathering login credentials or serving up malicious downloads.
They will resort to one of the following attacks if a hacker does not gain access to a local network connection.
1. Response Forgery Using the Birthday Attack
The DNS does not authenticate responses to recursive queries, so the cache stores the first response. To try to predict and give a forged response to the requestor, attackers use the “birthday paradox.” To construct a guess, this birthday attack uses math and probability theory.
In this case, the intruder is trying to guess your DNS request’s transaction ID, so before the real response, the fake response with the forged DNS entry gets to you.
A birthday attack is not a guaranteed success, but an attacker can sneak a forged reaction into a cache eventually. The attacker can see traffic from the fake DNS entry until the attack succeeds, before the time-to-live (TTL) expires.
2. Kaminsky’s Exploit
First, the attacker sends a DNS query for a non-existent domain to the target resolver, such as “fake.varonis.com.” The resolver then forwards the query to the authoritative name server to retrieve the false sub-domain IP address. The attacker floods the resolver with a large number of forged responses at this stage, hoping that one of those forgeries matches the original query’s transaction ID.
If successful, the attacker poisoned the targeted resolver’s DNS cache with a forged IP address for varonis.com, in this case. The resolver will continue to inform someone who asks it that before the TTL, the forged query is the IP address for varonis.com.
How To Detect DNS Cache Poisoning
But how can a DNS cache poisoning attack detect you? Track your DNS servers for potential attack signs. In order to keep up with the amount of DNS requests you would need to track, humans do not have the computational resources. In order to distinguish usual DNS activity from attacks, add data security analytics to your DNS monitoring.
A sudden rise in DNS activity on a single domain from a single source suggests a possible birthday attack.
An increase in DNS activity from a single source that queries several domain names without recursion from your DNS server suggests an attempt to locate an entry to be used for poisoning.
Track Active Directory events and File System actions for suspicious activity, in addition to DNS monitoring. And even better, to add important background to your cybersecurity plan, use analytics to compare behavior between all three vectors.
How To Protect Against DNS Cache Poisoning

You can make configuration changes on your DNS server beyond monitoring and analytics.
- To defend against possible targeted poisoning attacks, restrict recursive queries.
- Only data relevant to the requested domain is processed.
- Limit responses to being just for the domain requested.
- Force HTTPS to be used by customers.
Make sure you are using the new Connect and DNS app versions, so you have the latest security fixes.
If possible, make all remote clients connect via a VPN to secure traffic and DNS requests from local snooping, for example with remote employees. In addition, to further minimize risk, make sure that a good home Wi-Fi password is encouraged.
And lastly, use DNS requests that are encrypted. Domain Name System Protection (DNSSEC) is a DNS protocol that, to prevent forgery, uses signed DNS requests. The DNS resolver needs to validate the signature with the authoritative DNS server while using DNSSEC, which slows the whole process down. This has resulted in DNSSEC still not being widely embraced.
Recommended Articles
- Working Safely from Home – Online Security Measures in this Pandemic
- Importance of Web App Security over the Increasing Web Application Attacks
- Hybrid Cloud Security Puzzle: Integrated Solutions for Cloud Computing
- Make Sure Your Security Policies Survive the Transition to the Cloud
- Best Methods to Improve Information Security in Companies
- Healthy Ways to Guarantee Public Cloud Security: Best Practices & Guidelines
For the next version of DNS, DNS over HTTPS (DoH) and DNS over TLS (DoT) are competing requirements to keep DNS requests protected without sacrificing speed like DNSSEC. These are not ideal solutions, however, as they can delay or completely prevent locally performing DNS monitoring and analysis.
It is also important to remember that DoH and DoT will circumvent any parental controls that are performed on the network or other DNS level blocking. That said, Cloudflare, Quad9, and Google all have DoT-supported public DNS servers. These newer standards can be embraced by many new customers, but are disabled by default. More specific information on Varonis’s DNS security blog can be found.
DNS spoofing replaces the valid IP address of a website with the IP of a hacker’s machine. It can be especially difficult because of how difficult it is to spot, from the point of view of the end user, they have placed a perfectly normal-looking address in their browser’s URL bar.
It is not impossible to avoid, however. Via monitoring applications such as Varonis and using the DNS over TLS encryption protocol, risk can be mitigated.
DNS Spoofing FAQs
You can Ponder over some popular DNS spoofing questions answered below.
Q: Is DNS Cache Poisoning and the Same Thing as DNS Spoofing?
A: Indeed, the same cyber assault is alluded to in DNS spoofing and caching.
Q: How Does DNS Cache Poisoning Work?
A: By tricking your DNS server into saving a forged DNS entry, DNS cache poisoning works. Traffic to the forged DNS entry goes to the attackers’ server that chooses to steal information.
Q: To defend against DNS cache poisoning, which security features can be used?
A: Website owners should incorporate monitoring and analytics for DNS spoofing. This involves updating your DNS servers to DNSSEC or another encryption method, such as HTTPS over DNS or TLS over DNS. Usage of full end-to-end encryption such as HTTPS will also avoid spoofing wherever possible. Highly useful for this are Cloud Access Control Brokers (CASB).
By flushing the DNS cache of their browser regularly or after entering an insecure or shared network, end-users may reset a potentially spoofed DNS cache. On a local network, using a VPN will defend against DNS spoofing. The avoidance of suspicious links will help stop end-users from exposing the cache of their browser to danger.
Q: How can a DNS Cache Poisoning Attack be checked?
A: It can be hard to detect until the DNS cache becomes poisoned. Monitoring your data and shielding your devices from malware may be a safer strategy to protect them from compromises caused by a contaminated DNS cache.
To see how we use DNS monitoring to identify real cybersecurity threats, check out the Live Cyber Attack Lab.
Q: How Does DNS Communication Work?
- The browser will search its local cache first to see if the DNS data has already been saved.
- If the browser does not have the info, the next upstream DNS server will be asked which router will usually be on their local network.
- It will use an upstream DNS provider such as Google, Cloudflare, or Quad9 if the router does not have the necessary DNS entry in its cache.
- The DNS request will then be received by that upstream server and its cache verified.
- 4.1 Assuming that the DNS data is not already cached, a recursive DNS resolver will start by first querying the DNS root servers and asking “Who handles .com”
- 4.2 The resolver will then query the .com top-level domain server asking “Who handles Varonis.com,” and the TDL will then respond to the URL with an authoritative name server.
- 4.3 The resolver then issues a question asking “What is the IP of Varonis.com?” to the authoritative name server. “The authoritative name server then responds with the domain’s IP address.
Lastly, the DNS data is sent back to the end-computer user’s down the chain. Each DNS server will cache the response for future use along the way.
Q: How do Attackers Poison DNS Caches?
There is no single way a DNS cache can get contaminated, but some of the more common ways are: to make the victim click on malicious links to change the DNS cache in their browsers using embedded code. Hackers may also use a man-in-the-middle spoof attack to hijack the local DNS server. To redirect DNS requests to a DNS server managed by them, the attack uses ARP spoofing.
Q: What is DNS Cache Poisoning?
A: The act of replacing a DNS database entry with a malicious IP address that sends the end-user to a hacker-controlled server is DNS cache poisoning.
Q: How Is DNS Spoofing Done?
By gaining access and modifying a DNS cache or redirecting DNS queries to their own DNS server, a hacker conducts a DNS spoofing attack.
Q: What Is Meant By DNS Spoofing?
DNS spoofing means that the URL entered by a user on their browser, such as varonis.com, does not necessarily go to the valid IP address associated with that URL, but is redirected to a hacker-controlled malicious server instead.
Q: Why Is DNS Spoofing a Problem?
A: DNS spoofing is a problem because with any form of encryption, DNS is inherently trusting and sometimes not safe. This means that a DNS entry can be spoofed by a hacker and used for data theft, malware infection, phishing, and upgrade prevention.
Q: What are the Threats Posed by a DNS Spoofing Attack?
Data manipulation by the use of phishing pages is the prime challenge raised by DNS spoofing. In addition, by hosting legitimate-looking downloads that are actually infected with malware, there is a possibility of malware infection. Finally, if the device depends on the internet for changes, the updates can be avoided by modifying their DNS entries so that they do not end up on an actual website. As a form of censorship, this may also be extended to any website.
Terms related to how to detect dns cache poisoning
- dns cache poisoning example
- dns cache poisoning attack tutorial
- opendns cache poisoning
- dns cache poisoning is
- how to fix dns cache poisoning attack
- 2021/2022 dns spoofing
- what is dns cache poisoning infoblox
- best dns poisoning fix
- cybersecurity practices to protect DNS






