Recent Attack Trends Impacting Enterprises Worldwide with Ransomware. Best ransomware attack solution. Top ransomware removal tool is also highlighted. “A new warning about a “imminent cybercrime threat to U.S. hospitals and healthcare facilities” was issued by the FBI, CISA and HHS. Watch the “Protecting Healthcare Institutions from Recent Ransomware Threats” webinar on request to learn more about how to respond.
One of the most intractable and widespread challenges facing organisations in all sectors and geographies is ransomware. And, incidents of attacks on ransomware continue to grow. Meanwhile, in order to respond to changes that companies are making to rebound from these attacks, ransomware threat actors are changing their attack model.
As of September last year, ransomware triggered one in four attacks that IBM Defense X-Force Incident Response remedied this year. In June of last year, ransomware attacks started to burst. The month saw one third of all IBM Security X-Force ransomware attacks remedied so far this year.
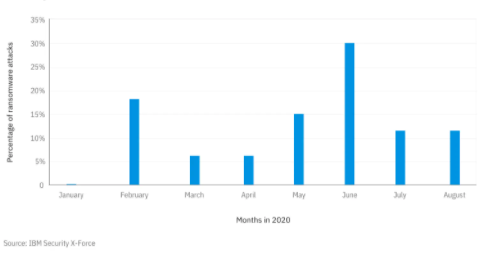
Figure 1: Relative monthly volume of ransomware attacks analyzed by X-Force (Source: IBM Security X-Force)
The value of ransomware for IBM Security X-Force is underscored by the strong toll this form of attack is taking on companies worldwide. By increasing ransom requests and assaults that combine malware with data manipulation and extortion tactics, this toll is made heavier.
Top Takeaways
- Demands for ransom are exponentially growing. IBM Encryption X-Force has had ransom requests of more than $40 million in some cases.
- Ransomware attacks by Sodinokibi account for one in three ransomware cases that IBM Security X-Force has responded to so far this year.
- Attackers find schools and universities to be an even more appealing target for ransomware attacks, especially when they digitally start classes or, according to COVID-19, play with hybrid environments.
- This year, 41 percent of all ransomware attacks evaluated by IBM Security X-Force attacked operational technology (OT) network organisations.
This article would demonstrate the forms of ransomware most commonly found by IBM Security X-Force. It would also cover some of the developments in ransomware attack tactics that are more important, such as hybrid extort-ransomware attacks, and what businesses can do to tackle this fresh attack from what may be a crippling threat to their activities.
Recommended Articles to Ransomware Attack
- Working Safely from Home – Online Security Measures in this Pandemic
- Importance of Web App Security over the Increasing Web Application Attacks
- Hybrid Cloud Security Puzzle: Integrated Solutions for Cloud Computing
- Make Sure Your Security Policies Survive the Transition to the Cloud
- Best Methods to Improve Information Security in Companies
- Healthy Ways to Guarantee Public Cloud Security: Best Practices & Guidelines
Ransomware Attack Trends
The number of ransomware attacks remedied by IBM Security X-Force Incident Response more than tripled relative to the previous year, looking at data from Q2. Between April and June last year, they represent 32 percent of the events our staff reacted to.
Attacks
A general improvement in ransomware attacks has been detected by IBM Security X-Force in terms of goals. Ransomware strikes engineering firms hardest. This constitute about a fifth of all events referred to this year so far. The professional services market is the second most attacked industry and 17 percent of ransomware attacks have been experienced. Thirteen per cent of attacks are preceded by government organisations in third place.
Attacks on these 3 sectors show that ransomware threat actors, such as industrial networks, are finding victims with a poor tolerance for downtime. Because of a pause in activities, companies that need strong uptime will lose millions of dollars daily. Therefore, to restore access to data & resume tasks, they will be more likely to pay a ransom.
IBM Technology X-Force has also reported an increase in ransomware attacks on public institutions last year, in addition to these industries. Because of COVID-19, attackers find them to be an attractive target for ransomware attacks, especially when schools & universities digitally start classes or experiment with hybrid environments.
In August and September, a cluster of universities targeted in May and June last year extended to additional academic institutions, with universities paying ransoms ranging from $400,000 to over $1 million in the expectation of not publicly revealing classified information on professors, students and studies.
Geo Reach
Although ransomware attacks continue to strike all corners of the globe, the worst hit so far this year are Asia and North America. They account for 33 percent and 30 percent, respectively, of IBM Security X-2023 Force’s ransomware commitments.
In recent months, Europe has also witnessed major ransomware violence, comprising 27 percent of the attacks remedied by IBM Security X-incident Force’s response unit. These statistics show that, while typically geography-agnostic, ransomware attacks appear to concentrate on areas more heavily inhabited by companies they can target.
Evolving Ransomware Tactics this Year
This technique puts multiple victims in a state of catch-22. They can suffer a data breach, destruction of data and consumer information even though they are able to recover encrypted files from backup, and have to face regulatory penalties, not to mention rebuild a ruined reputation.
In certain cases, in order to make them contemplate paying, criminals were accused of calling their ransom according to the regulatory penalties companies would have to face, using it as another intimidation technique.
Ransomware threats are now being data hacks, with the related danger and repercussions that these kinds of events include, with criminals potentially stealing company data. This pattern forces security administration to re-assess risk and properly change emergency response, crisis recovery and business continuity plans.
Sodinokibi: Linked to Organized Crime Group ITG14
Sodinokibi (also known as REvil), a ransomware-as-a-service (RaaS) threat model that has been capitalising on mixed ransomware and extort attacks this year, is the ransomware strain IBM Defense X-Force has seen most often this year.
This malware has been used in ransomware and data manipulation attacks, and in some circumstances, although they were unable to coerce users to pay up, the operators stole and auctioned off confidential data on the internet.
Sodinokibi also accounts for 29% of all IBM Defense X-Force ransomware commitments last year, showing that, relative to other ransomware strains, Sodinokibi attackers are more advanced in obtaining access to victim networks.
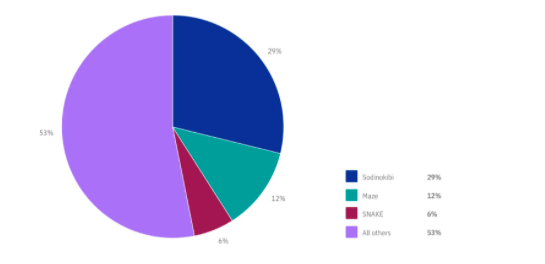
Figure 2: Top attacking ransomware families per IBM Security X-Force engagements (Source: IBM Security X-Force).
Sodinokibi Claims for Ransomware Attack
From our study, since its formation in April, Sodinokibi has claimed at least 140 victim organisations, with the top sectors targeted, including the wholesale sector (19%), manufacturing (18%) and professional services (16 percent ). Sodinokibi has been hardest struck by U.S. organisations, making up nearly 60% of those enduring its attacks, followed remotely by the U.K., Australia, and Canada.
More than 36 percent of Sodinokibi victims have paid the ransom, according to IBM Security X-estimate, Force’s and 12 percent of victims have had their sensitive data sold on the dark web at an auction. Data values vary from $5,000 in these auctions to over $20 million. Furthermore, we believe that at least 32% of users of Sodinokibi ransomware have had their data leaked by those running this ransomware.
Trending Security Articles
- DNS Spoofing- How To Prevent DNS Cache Poisoning
- Policy & Cloud Security Compliance Standards.
- How to Avoid DNS and DNS Spoofing Poisoning
- 9 Potential Threats hindering the Promotion of Cloud Computing Industry
- Cloud Computing and Enterprise Computing faces the same Security Threats
Our analysis also suggests that Sodinokibi attackers regard the annual revenue of a victim organisation when assessing a ransom request, with known demands varying from 0.08 percent to 9.1 percent of the annual revenue of the victim organisation. The group seems to tailor its demanded ransom payment to a victim organisation, with $42 million being the highest reported ransom amount sought by Sodinokibi and about $1,500 the lowest. For Sodinokibi ransomware gains, the optimistic prediction is at least $81 million.
First of all, we found facts during the Sodinokibi ransomware research showing that ITG14, which shares campaign overlap with FIN7, is at least one partner group related to these attacks.
Secondly, we discovered that this Carbanak sample was identical to recent Carbanak 64-bit versions, which were linked to ITG14 tools and techniques, after researching a Carbanak backdoor affiliated with a Sodinokibi ransomware attack.
Thirdly, we also test the use of this study strictly by the community. This leads one to believe that ITG14 is at least one affiliate party that contracts to deliver these attacks with Sodinokibi RaaS providers.
Maze: Using the Buer Loader
In 2021, IBM Defense X-Force also detected continuing Maze ransomware attacks, which accounted for 12% of the ransomware attacks observed this year so far. Maze also uses RaaS and mixed versions of extort-ransomware and advertises its victims on a blog that is freely accessible, close to Sodinokibi’s techniques. In the professional services market, Labyrinth has heavily attacked victims, mainly striking organisations in North America and Europe.
Multiple threat groups offer Maze ransomware to companies under the RaaS model, creating a broad range of methods, techniques and procedures (TTPs) that can be correlated with Maze ransomware, as many technology vendors have illustrated. Of these TTPs, one possibly newly discovered technique was found by IBM Security X-Force: the use of a code-signed Buer Loader to maintain a foothold.
In late 2yrs ago, Buer Loaders first emerged for sale on the dark web, and received numerous updates. It can download and execute additional payloads, create persistence and communicate over the protocol of HTTPS. The intruder has possibly used the Buer Loader, a very popular method used in Maze attacks this year, to download and instal Cobalt Hit.
Figure 3: Buer Loader version released in May
SNAKE/EKANS: A New Threat to Industrial Controls
EKANS, or SNAKE (EKANS spelt backwards), which was first detected in mid-December last year and makes up 6 percent of the ransomware attacks that IBM Security X-Force has observed so far this year, is one of the most important ransomware strains.
On a victim’s computer, EKANS ransomware is able to destroy many vital processes, including several processes specifically connected to the activities of the industrial control system (ICS).
Given that this ransomware has the ability to have a larger influence on physical processes relative to other ransomware variants, this function has important repercussions for ICS and operational technology (OT)-connected networks. The consequences of possible EKANS attacks are important as 41 percent of all ransomware attacks observed by IBM Security X-Force this year attacked OT-connected industries.
IBM Security X-Force review of samples of EKANS ransomware suggests that it was written in an open-source initiative, the Go programming language. As a first step, the ransomware tries to address the inner domain name of a victim.
If the domain name can not be fixed by the ransomware, it uses this move as a kill switch and terminates. Additionally, before the encryption process takes place, the malware scans for many hardcoded ICS-related processes to kill.
This part of the malware is identical to MegaCortex, for which many changes have been evaluated by IBM Security X-Force. In fact, in addition to dozens more, the twelve hard-coded processes EKANS is designed to destroy can be found in the MegaCortex ransomware.
Combating the Ransomware Onslaught
In several ways, ransomware attack tactics have placed victims in a more daunting role than we have historically seen. Many that use ransomware to extort people have increased demands over time, raising in some instances to over $40 million. Some ransomware exploits the most sensitive networks and operations of organisations by mixing assaults with extortion tactics.
Any companies could be tempted to pay ransom if attackers are able to gain access into a network, encrypt files and attempt to leak stolen data. A choice to pay requires several considerations, and no particular estimate would be applicable to all organisations.
“The FBI does not support paying a ransom in response to a ransomware attack. Paying a ransom doesn’t guarantee you or your organization will get any data back. It also encourages perpetrators to target more victims and offers an incentive for others to get involved in this type of illegal activity.”
If your company has become a target of ransomware, we suggest looking for a workaround where it is possible to recover data and minimise reputational damage, rather than paying the perpetrators. IBM Encryption X-Force malware reverse engineers have been able to build a custom decryptor to retrieve encrypted files in certain cases of ransomware assaults. Although this approach appears to be the case rather than the law, until resorting to paying a ransom, it underlines the value of pursuing a number of alternatives.
Arguably, Ransom payments encourages attackers to continue their operation, justify their business model, and enable additional cybercriminals to engage in this form of attack.
Steps to Reduce Risks and Minimize Damage
Also in these tough circumstances, though, there are steps that organisations can take that can help reduce risks and alleviate damage.
- Establish and maintain offline backups: Ensure you have read-only keys to files securely stored from intruder usability. Backup file availability is a big differentiator for companies and can help rebound from a ransomware attack.
- Implement a policy to avoid illegal data theft, notably when it relates to the upload of massive volumes of data to legal cloud storage sites that can be exploited by attackers.
- To detect future security incidents, hire customer behaviour analytics. When activated, presume that an infringement has occurred. Audit, report and respond effectively on alleged violence associated with privileged accounts and classes.
- Using multifactor authentication in an enterprise network on all remote access points, with special care to protect or disable access to remote desktop protocol (RDP). It has been recognised that numerous ransomware attacks leverage poor RDP access to obtain initial entry into a network.
- Using penetration testing to find weak points and flaws in enterprise networks that can be prioritised for patching. In specific, we suggest the introduction of CVE-2019-19781 mitigations, which have been used by several threat actors to gain initial entry into businesses in 2021, including for ransomware attacks. Furthermore, consider prioritising the rapid remediation of the following commonly abused security vulnerabilities, as applicable:
- CVE-2019-2725
- CVE-2020-2021
- CVE-2020-5902
- CVE-2018-8453
VPN-related CVEs
- CVE-2019-11510
- CVE-2019-11539
- CVE-2018-13379
- CVE-2019-18935
Watch our webinar, Combatting Ransomware: How Threat Intelligence Improves Security for the City of L.A., on demand, to learn more about X-Force threat intelligence on ransomware assaults.
Topics related to Ransomware Attack
- What is ransomware attack meaning
- recent ransomware attacks
- Best ransomware attack solution
- Ransomware Attack
- New ransomware meaning
- List of ransomware attack examples
- Biggest ransomware attacks
- Top ransomware removal tool
- Wannacry ransomware attack
Finally, this is the Ransomware Attack Trends Affecting Organizations Worldwide. Please share your stories if you have encountered a ransomware attack and would like urgent assistance from tech companies.
Check out these related posts to Ransomware Attack.
- 9 Best WiFi Penetration Testing Tools Hackers Use
- Security Strategy Planning Guide to Prevent DNS Attacks
- Top Rated Unified Security Management Software
- Beware: E-Commerce Skimming is the New POS Malware







