Linux Security in Amazon EC2 – Amazon Elastic Compute Cloud. Amazon Linux 2’s default protection settings may not be the most robust. I’ll try to illustrate in this short write-up how a few of these setups can be hardened from a security viewpoint. Let’s get started with the explanation. Amazon Linux Security Hardening Script Guide.
Upgrading OpenSSH to latest available version:
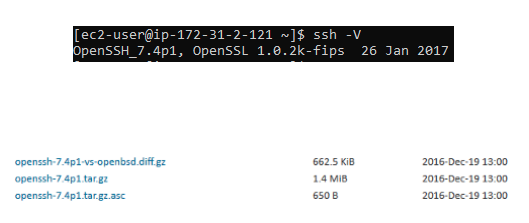
The stock package of Amazon Linux comes with OpenSSH v7.4
To be sincere, this particular release happened sometime on 2016-Dec!!!
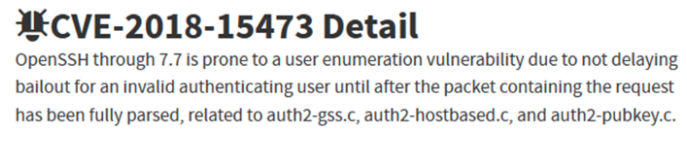
Several vulnerabilities have been documented on these older versions of OpenSSH, with the user enumeration attack as monitored by CVE-2018-154733 being the most prominent.
The Upgrade Guide
Without further ado, let’s upgrade NOW!
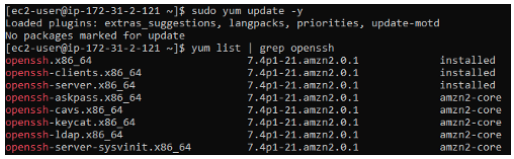
Take this word of caution: trying to instal using the tried and trusted sudo yum update process would fail since the OpenSSH kit will not be picked up during the upgrade.
The best course of action will be to import the most recent available version from openbsd.org, add all appropriate dependencies, and compile/install the package for upgrade. Oh, my goodness! That’s a great deal of work… Ok, don’t worry, as I’ve got you protected.
Use this convenient little script to do this for you and maybe you can thank me for this article by clapping on it.
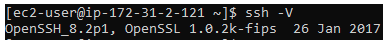
Immedialy you run it, you should be able to see the upgraded SSH version.
SSH upgrade to the strongest available KeyExchanges & Ciphers:
Amazon Linux 2 contains cryptographically weak Ciphers and KeyExchange algorithms that have been shown to be vulnerable to attack.
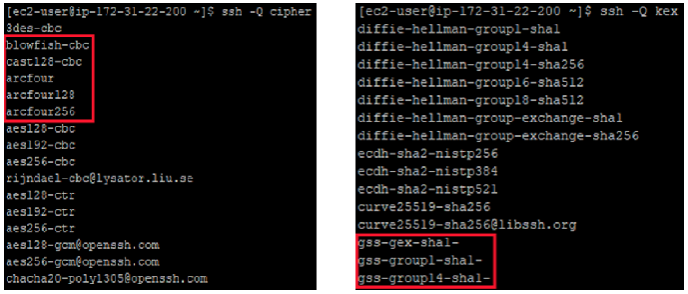
Birthday attacks and Logjam-style attacks are two known attacks that can break SSH security by using the above weak ciphers/kex.

Just the best ones should be held for negotiations when creating client<->server communication. So, how do we go about doing it? You already have the new Ciphers & KeyExchanges if you followed the first part of this blog in updating the OpenSSH version. After the update, you just need to re-enable the powerful ones.
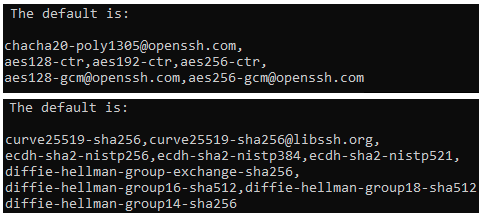
To get the new values after the new OpenSSH update, go to the man page for sshd config and check for Ciphers and KexAlgorithms.
Other Linux Topics
- Top Kubernetes Courses Online – IT & Software Development [Udemy]
- 10 Free Kubernetes Courses Online Tutorials [Udemy]
- Linux Operating Systems for Kubernetes – OS Support
- DevOps Kubernetes Course Content [Beginner’s Guide]
Edit the /etc/ssh/sshd_config file now to add the default values given above in the prefered order as shown below:
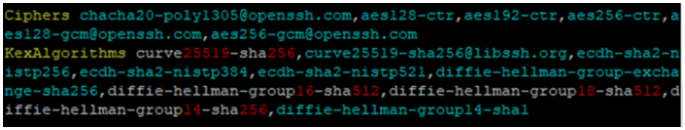
Now, Restart (sudo /etc/init.d/sshd restart) the sshd service. Lo and behold your SSH is hardened to take on the big bad world of internet!
Related Topics to Amazon Linux Security Hardening Script Guide
- amazon linux ami hardening script
- amazon linux 2 cis hardening script
- amazon linux 2 hardening guide
- amazon linux 2 hardening script
- amazon linux 2 cis benchmark
- amazon linux hardening
- amazon linux cis hardening script
- ec2 security
Certifications
- 2021 Best Salary Paying IT Certifications in-Demand
- Container 101 Tutorials: Kubernetes Technology
- Microsoft Certifications with Highest Salary in Demand 2021
- Most in-Demand IT Certifications for Beginners & Pros
- 10 Best Udemy Kubernetes Courses & Tutorials [2021]






