Two-factor authentication (2FA) –or multi-factor authentication (MFA) in general – has grown in importance in security in recent years. This is about how users (employees and customers) authenticate to systems. Authentication by username and password is called 1FA.
However, in order to increase safety, 2FA or MFA has been increasingly used in recent years. One possibility for a second factor is the Time-based One-time Password (TOTP) method, which is probably the best known method used in countless applications. For example, the TOTP procedure is used by Google and Microsoft in the Authenticator app.
Many may also remember the tokens of e-banking systems, which had to be renewed every 60 seconds. This combination between username/password and a second system, which is mostly based on personalized hardware such as your mobile phone, is considered to be 2FA.
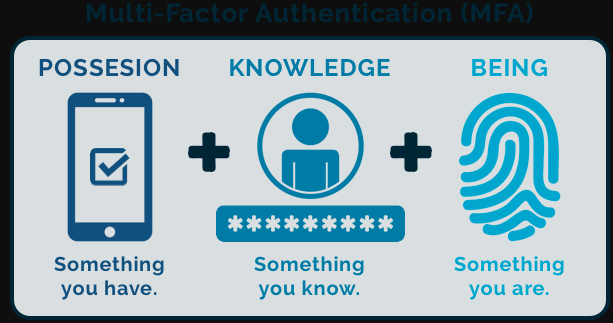
The possible authentication factors can be divided into three different categories:
- Knowledge: the user has certain knowledge, which is known only to him. For example, these are passwords, pins, or answers to security questions
- Biometrics: the user clearly uses biometric features such as his fingerprint, face or iris pattern
- Hardware: the user owns an item that helps him with authentication. This could be a code generator, an SMS or an email to his mobilt elefon. Or hardware in the form of a card or token.
Challenges of Multi-Factor Authentication (MFA)
- Data is more secure from third-party access. Usernames and passwords of customers and employees are vulnerable to theft. They are either not complex enough (in many cases only a few letters such as “123456”) or can be read out by Trojan. Another vulnerability is the writing down of passwords, either physically or digitally. 2FA / multi-factor authenticati
on can prevent attacks despite successful password entry. - They increase their reputation towards customers. Many customers don’t mind taking an extra step when they know it serves their safety. They gain additional trust when they know that the security of their data is important to the company.
- Productivity can be increased or maintained. As data access becomes more secure, employees can increasingly be allowed to work from home. In times like the current coronavirus crisis, it helps to maintain productivity. In normal times, employees can increasingly access the systems from home or on the go. According to the Harvard Business Review, this can lead to an increase in productivity of up to 13% (Harvard Business Review).
- Lower operational costs. Access for hackers is made more difficult and this can minimize system failures. The EU-wide GDPR Guidelines, as well as the Data Protection Act adapted to Switzerland, requires notification to the Confederation if personal data is lost, deleted, destroyed or altered or if unauthorised persons are disclosed or made available to persons (Art. 4 lit. g E-DSG). Improved security measures can prevent fines.
- Armed for possible standard. 2FA or MFA can be used by the Federal Council as a standard for companies with sensitive data with regard to data security (Art. 7 Data Security & Art. 11 E-DSG).
Related searches
- azure multi-factor authentication
- Amazon multi factor authentication (mfa login)
- Microsoft multi factor authentication app
- multi factor authentication benefits
- two-factor authentication examples
- back to basics multi factor authentication mfa
- multi-factor authentication can be used to handle spoofing
- Fortnite multi factor authentication
Organizations that are serious about security have no choice but to implement multifactor authentication. It is currently a recognized and proven practice to authenticate users with multiple factors to protect sensitive data. Finally, we looked at the Multi-Factor Authentication (MFA) – Login, Benefits, Examples. Next article will focus on What’s the Difference Between Two-Factor Authentication and MFA?