Advanced File Permissions in Linux. Manage Changing Team Needs with Advanced Permissions. Configure Advanced Permissions with these guide I have provided in this article. Its a continuation of UNIX & Linux File Permissions PART 1. Full details on Managing Linux File Advanced Permissions Read/Write & Change — Part 2.
If you landed on the page from a search engine, then you can find Part 1 of this series of UNIX & Linux File Permissions | Read/Write & Change here.
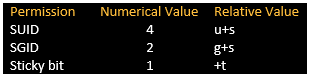
Keep in mind that there are three advanced permissions — set user ID (SUID), set group ID (SGID) and sticky bit. Let’s take a closer look at each of these permissions:
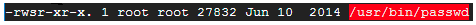
A user can sometimes need special permissions in order to complete a particular task (for e.g change his password). This will necessitate writing to the /etc/shadow file, which is write-protected for users without root access. SUID is useful in these cases, and the utility to change one’s password (/usr/bin/passwd) has it allowed by default.
Linux File Permissions Outputs
Written below is the output of 1s -1 which shows an s at the position of x in ‘user rights’ column:
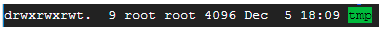
The sticky bit, which is the last of the special permissions, comes in handy in shared environments. This happens where several users have write permission and you need to protect your files from accidental deletion. This permission is allowed by default in the /tmp directory.
This is the output of ls -1 which shows a t at the position of x in the ‘other rights’ column:
It’s also worth mentioning that when these special permissions are extended to files and folders, the results differ.

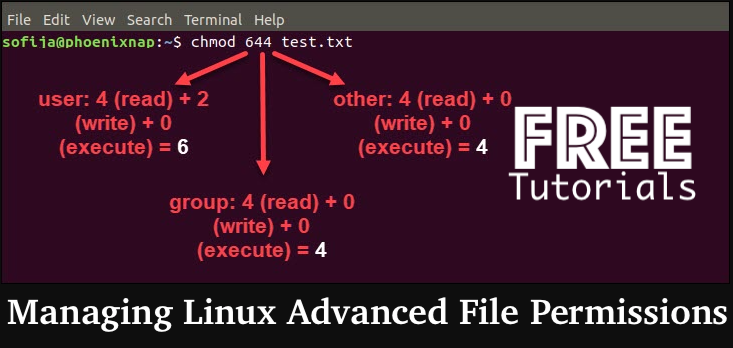
These permissions are set with the chmod command. They also have numerical values, making it simple to refer to and control.
Now, let’s take a good look at few examples with these additional permissions:
First of all, take note of the extra digits at the start represent the sticky bit, SUID, and SGID, respectively.
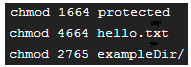
Calm down, we’re not quite done yet. There’s also a smidgeon of a difference for all three advanced permissions, which are represented by S and T. (both in capital letters). Find the following 1s-1 listing:
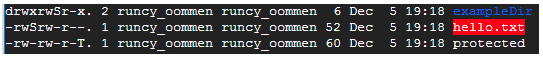
In summary, this means that the SUID, SGID, and sticky bit have been added to the above file/directory, but the execute bit has not been set (x). They will be represented as s and t if the execute bit is set (both small letters).
Conclusion:
This is my conclusion segment. With this part 2 blog series, I hope to have educated you on Linux permissions and hopefully broadened your perspective on dealing with files and folders. Finally, in the comments section, please let me know your suggestions (bouquets and brickbats).
Related Topics for Managing Linux File Advanced Permissions
- 4096 permissions
- advanced permission in linux
- permission code
- special permissions in linux
- linux user group permissions
- change file attributes linux
- what is file permission
- octal permissions linux
Trending Articles
- Amazon Linux Security EC2 Hardening Script Guide
- Talos OS v0.7 Platform – Modern Systems Kubernetes
- Linux Operating Systems for Kubernetes – OS Support
- Container 101 Tutorials: Kubernetes Technology
- Container 101 Tutorials: Kubernetes & Docker Technology
- Kubectl command – How to Add or Remove Labels to Nodes in Kubernetes