firewall - search results
If you're not happy with the results, please do another search
Linux Operating Systems for Kubernetes – OS Support
This is a complete guide to Linux Operating Systems for Kubernetes containers. Learn more about Container 101 Tutorials for Beginners: Kubernetes Technology. It also...
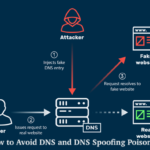
How to Avoid DNS and DNS Spoofing Poisoning
DNS "spoofing" and "poisoning". The name literally conjures up the kind of thoughts that hold network administrators up throughout the evening. What if he...
Security Strategy Planning Guide to Prevent DNS Attacks
When planning your cyber security strategy, don’t forget your DNS. Cyber Security Planning Guide from Federal Communications website. This is a Step by Step...
How to Secure your System against DNS attacks
This post will show you How to Secure your System against DNS attacks. First of all, to address this growing threat, Palo Alto Networks...
Top Rated Unified Security Management Software
This article contains 14 top Unified Security Management Software. Business functions are increasing every day and with the additional costs of adding resources to...
Security Management in Unified Cloud Platform: Why Companies Need it
Latest Cloud Security Management: Technology is advancing, therefore we must adapt the way we secure data to today’s needs and the future. You will agree...
Why Public Cloud must Ensure Reliability and Security
The Centre for International Field (CIF) research shows that there are still a lot of inexperiences in public cloud computing, a relatively new IT delivery model. Pharro said:...
Cloud Computing & Mobility expose the Limitations of Existing Networks.
Limitations of Existing Networks over Cloud Computing & Mobility. In today’s corporate networks, the highly virtualized environment, coupled with the surge in mobile traffic,...
Cloud Data Center Computing Environment Security Solution
The Information Security Conference: The theme of this conference was "New Opportunities for Information Security-Big Data, BYOD, SDN, Cloud Security". Tech guys from the Information...
Simple and Practical Cloud Computing Security Tips
We have updated the Simple and Practical Cloud Computing Security Tips so that you can know the Security threats in cloud computing and preventive methods. Nowadays, cloud...