This article contains 3 Ways to Ensure Your Security Policies Survive the Transition to the Cloud. By the year 2024 the amount of data stored in the cloud by both governments, organizations, and individuals will exceed 75 Zettabytes. This is an estimated forty nine percent of the world’s 175 zettabytes of data at that time. As a matter of fact, this trend has no doubt been accelerated by COVID 19 pandemic. This is so because as organizations have been forced to shorten cloud migration timeframes to ensure business continuity during the epidemic.
As the cloud continues to grow wider as one of the key business enablement tools for organizations post-COVID-19, what’s undoubtedly also true is that businesses still trying to understand their security obligations in the cloud. This is the main reason we decided to discuss the importance of having strong security policies and implementing them correctly as your company moves to the cloud.
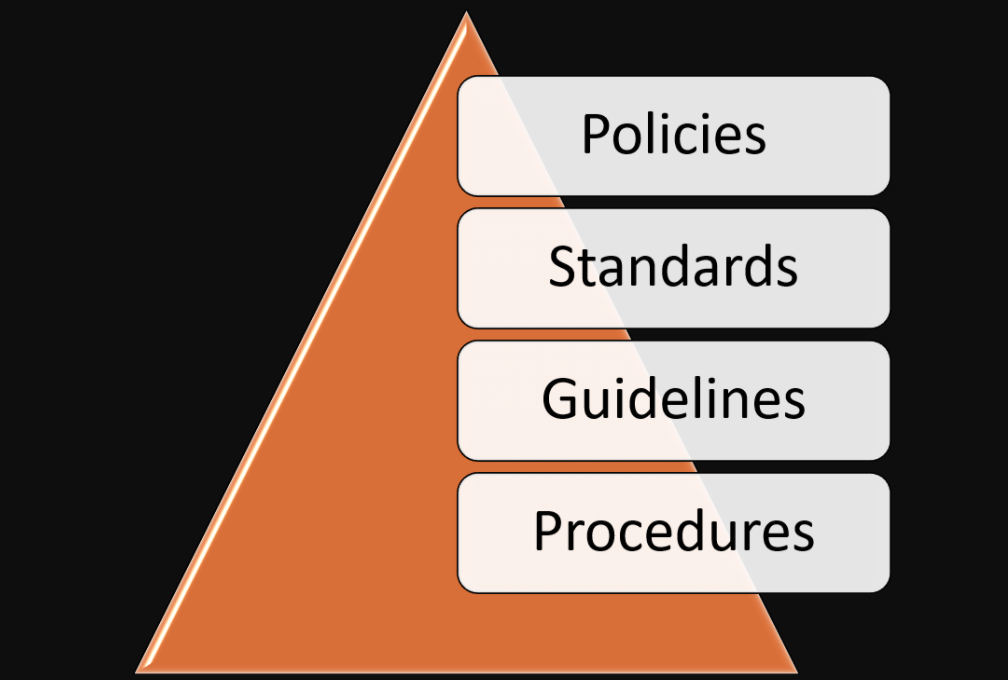
What is Security Policy? Definition!
Wikipedia says Security policy is a definition of what it means to be secure for a system, organization or other entity. For a company, it addresses the constraints on behavior of its members/staffs as well as constraints imposed on adversaries by mechanisms such as doors, locks, keys and walls.
Start with a cloud-native, security first mindset
Sometime ago in July, our team wrote an article about ITProPortal talking about the importance of a security-first, cloud native mindset. Even though most businesses face mounting pressure to move to the cloud, especially after COVID lockdown, this pressure does not alleviate the need to secure the cloud. Just as the shared responsibility model is common to most cloud services providers suggests, it’s invariably wrong to assume that cloud environments are “secure by default.”
To be candid with you, this is because It is your organization’s responsibility to determine what security controls and configurations are sufficient for satisfying your organization’s specific data security and data compliance requirements. You should bear in mind that the failure to make this consideration will result in your organization relying on security through obscurity rather than practices and policies that actively improve your security posture in anticipation of cloud security threats. Its simply like; you should not leave the front door to your house unlocked before going to bed. Therefore, you should ensure your organization takes steps to secure its cloud systems.
The cloud-native, security first mindset requires your organization to consider several things, including:
- What business functions are migrating to the cloud?
- Which types of sensitive data are central to those processes?
- What settings and controls will be deployed to ensure visibility and protection of that data
- And finally how to implement policies that complement the settings and controls you seek to put into place.
Let your data guide which policies you maintain in the cloud
While understanding that security should be your first and foremost concern in the cloud, it isn’t enough to simply lift your existing security policies as they exist within your on-prem environment and try to force them to work in the cloud. As can be seen that cloud environments having significant differences from other, more traditional environments, organizations may have to more or less redesign their policies from the ground up to work in the cloud.
In the light of this, the redesign and implementation process should be data-centric, which means that rather than assuming what controls and processes should be in place, you determine which ones work best by taking inventory of the types of data you’re trying to secure. In this vein, this should include the classification of the data as well as knowledge of the location of this data within your cloud environments and knowledge of which resources have access to this data.
The main reason why a data-centric approach is favored in the cloud is because the cloud is parameterless and as a result, data in the cloud tends to be permeable. Data from the cloud can be accessed by or potentially stored onto any connected devices and as such, approaches that overemphasize network or endpoint modalities (which are myopically concerned with securing networks and physical assets) might fail to capture a holistic view of your security posture.
Keep in mind that the specifics of how to build and implement a data-centric security program will depend on your compliance and security needs. Take for instance, regulations like HIPAA (Health Insurance Portability and Accountability Act) explicitly require organizations to put access controls into place and document attempts to access protected health information (PHI). You will agree that this effectively spells out the need for a control like data loss prevention (DLP). However, even in the absence of such requirements, some form of data classification and access controls for your data will likely be essential to your security program.
Invest in the right tools to manage data policies
Another important consideration is the question of how you intend to maintain the visibility and control necessary to monitor your data and implement necessary changes to your environment’s security. In addition to access controls and data discovery tools, security platforms that provide a centralized location for you to manage your data security policies.
Generally, look for a platform that provides a policy engine to coordinate machine learning detectors to alert on specific types of sensitive data and create appropriate workflows in response to these alerts. For example, in healthcare, tokens like names and addresses wouldn’t be considered protected health information (PHI) unless associated with a specific patient medical record.
Finally, you might then choose to set a rule for detectors in Slack to only have Nightfall alert on addresses when they appear next to another form of PHI like a name or social security number, thus more appropriately codifying what your PHI breach risk actually looks like. In the long run, please Make Sure Your Security Policies Survive the Transition to the Cloud.