Microsoft - search results
If you're not happy with the results, please do another search
Cloud Computing & Mobility expose the Limitations of Existing Networks.
Limitations of Existing Networks over Cloud Computing & Mobility. In today’s corporate networks, the highly virtualized environment, coupled with the surge in mobile traffic,...
Cloud Data Center Computing Environment Security Solution
The Information Security Conference: The theme of this conference was "New Opportunities for Information Security-Big Data, BYOD, SDN, Cloud Security". Tech guys from the Information...
Cloud Computing needs Complete Security Standards
Cloud Security Standards: A recent study by Gartner predicts that all cloud businesses will continue to grow in double digits. Therefore, Cloud Computing needs...
Robotics: What Technologies do Cloud Robots Need?
The technological development momentum of the modern world is swift and violent. What Technologies do Cloud Robots need to Escort? The "new generation of information technology" along...
Why Data Analytics Skills is In-Demand: Salary Quotes
This post contain reasons why Analytics Skills are Highly Sought After! What does this mean? Data Analytics involves processing structured and unstructured Data sets...
Cloud Computing Model in the Development of the Internet
Cloud computing is an increase, use, and delivery model of Internet-based related services, which usually involves the provision of dynamic, easily scalable and often...
4 Common Cybersecurity Threats – When You are Not at Home
This is an explanation of 4 Most Common Types of Cybersecurity Threats. There’s every indication that the pandemic is changing the nature of cybersecurity. Online...
Setting up Windows Container Service on a Kubernetes Cluster
A step-by-step guide to setting up a Windows container worker node and a sample app on AWS EKS. This is to simply to support...
Shared Responsibility Model – Adopting AWS (and Other Cloud Services)
For IT tech guys to understand the shared responsibility model of cloud services is however one of the most important aspects of cloud security....
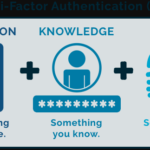
Multi-Factor Authentication (MFA) – Login, Benefits, Examples
Two-factor authentication (2FA) –or multi-factor authentication (MFA) in general – has grown in importance in security in recent years. This is about how users...