devops - search results
If you're not happy with the results, please do another search
DevOps Engineer’s Guide to Kubernetes Operating Systems
This is the DevOps Engineer's Guide to Kubernetes Operating Systems. Now that you've decided to use Kubernetes (or thinking about exploring some Kubernetes deployments.)...
DevOps and Containers | Benefits, Metrics, Challenges & Risk Management
What is DevOps? What are the roles of Containers in DevOps? In this article, we are going to talk about all the Benefits, Metrics,...
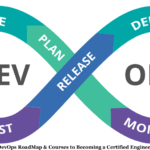
DevOps RoadMap & Courses to Becoming a Certified Engineer
This is the Complete DevOps RoadMap you can use become a certified tech engineer to apply a get a high paying job in the...
DevOps Kubernetes Course Content [Beginner’s Guide]
Udemy DevOps Kubernetes Course Content . Learn DevOps: The Complete Kubernetes Course. Kubernetes will run and manage your containerized applications. Learn how to build,...
[Udemy] Learn DevOps: The Complete Kubernetes Course
Learn DevOps: The Complete Kubernetes Course. Learn DevOps: Advanced Kubernetes Usage. Kubernetes will run and manage your containerized applications. Learn how to build, deploy,...
10 Interview Questions on Kubernetes for SDET/Devops Set-03 (ReplicaSet in K8S)
This is a list of 10 Interview Questions on Kubernetes for SDET/Devops Set-03 (ReplicaSet in K8S). It is required for those who are applying...
FBI’s Cybersecurity Strategy to Fight Cyber Crime impose costs on Adversaries
Malicious cyber activities pose serious threats to public safety, national security, and our economic well-being. The FBI's cybersecurity strategy centers on imposing risks and...
How Criminals Carry Out BEC Scams and How to Protect Yourself
Business Email Compromise (BEC) scams, also known as email account compromise (EAC), stands out as one of the most financially devastating cybercrimes. It capitalizes...
Did you know that FBI Email System was Hacked to Send Out Fake Warnings?
The FBI office email system was hacked in 2021, allowing hackers to send out fraudulent warnings. This breach occurred due to a flaw in...
FBI successfully dismantles Qakbot Botnet and removed the Malware
In the news today, FBI’s Duck Hunt operation takes down Qakbot botnet, saving 7 lakh machines globally. The U.S. government's domestic intelligence and security...



![DevOps Kubernetes Course Content [Beginner’s Guide] DevOps Kubernetes Course Content [Beginner's Guide]](https://hybridcloudtech.com/wp-content/uploads/2021/02/DevOps-Kubernetes-Course-Content-Beginners-Guide-150x150.png)
![[Udemy] Learn DevOps: The Complete Kubernetes Course Udemy Learn DevOps 2021 - Complete Kubernetes Course](https://hybridcloudtech.com/wp-content/uploads/2021/02/Udemy-Learn-DevOps-2021-Complete-Kubernetes-Course-150x150.png)




