We are already in the holiday season. But as the holiday shopping season shifts into hottest zone, the Corona Virus (COVID-19) pandemic is growing into an ongoing 2021 trend. And now consumers are switching to online buying. But Beware: E-Commerce Skimming is the New Point of Sale (POS) Malware.
Tags: E-commerce | E-commerce Transactions | Online Shopping | POS Malware
Instead of flooding brick-and-mortar superstores — and point-of-sale (POS) machines — with sales, new studies suggest a high percentage of shoppers in 2020/2021 will be using online options and e-commerce checkout pages for payment. And, those checkout pages are exactly what cyber criminals are targeting — inserting secret malicious codings into them that will send payment card data directly back to the attackers in a technique some refer to as e-skimming.
In the first place, malicious cyber actors, shift to online commerce with some implications. One of which is using POS malware to steal payment card data is less profitable than it once was, especially when compared to exploiting vulnerable e-commerce checkout pages of organizations.
There is a supporting data from IBM Security X-Force which throws light on POS malware use. There’s a significant increase in e-commerce card skimming and a general cyber criminal exodus from the POS malware forefront. Furthermore, with more shoppers choosing online sales this year — a development some analysts expect will persist beyond the Covid-19 pandemic — these trends are likely to grow over time.
E-commerce Threats on the Increase
The data from X-Force shows incidents involving e-commerce threats which increment nearly reach 400% since the year 2018. Trust me, some of these incidents that is occurring has involved attacks from a team/groups called Magecart, where threat actors inject malicious JavaScript code into e-commerce checkout pages, sending payment card data directly to the attackers.
Bear in mind that other incidents have included SQL injection to exfiltrate data from externally hosted e-commerce servers or the creation of fake subdomains to commit fraud on e-commerce websites.
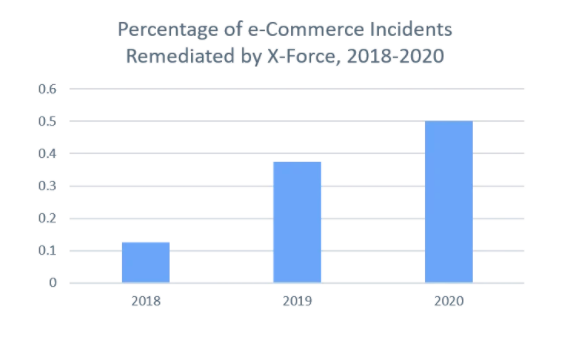
Figure 1: E-commerce incidents remediated by X-Force Incident Response, as portrayed as a percentage of total incidents from 2018-2020 (Source: X-Force)
Related
- Why Public Cloud must Ensure Reliability and Security
- Cloud Computing is fighting to Protect your Information Wealth
- Cloud Data Center Computing Environment Security Solution
- Cloud Computing needs Complete Security Standards
Rising E-commerce Skimming Sophistication
As attackers focus additional energy on e-commerce card-skimming operations, their tactics have become increasingly sophisticated.
A very good example is online card skimmers that input malicious JavaScript codings into e-commerce checkout pages. This has evolved to incorporate anti-forensic techniques, such as self-removal, to make detection and analysis of the malicious code more difficult.
In other cases, attackers have used forms of steganography to hide malicious code in images on the compromised site, as well as the stolen payment card data while exfiltrating it from compromised websites.
In addition, for threat actors involved in e-commerce skimming, checkout pages built on the same platform can enable attacks against multiple victims at once. In July 2020, researchers revealed that a Magecart group IBM tracks as Hive0059 (aka Magecart Group 8 or Keeper) compromised over 570 online shops over a three-year period.
Of the compromised sites, 85% used the same underlying platform. With e-commerce skimming attacks, one vulnerability can help attackers automate the same attack for many others, harvesting card data that can impact a large number of shoppers.
As e-commerce is set to explode this holiday season, card skimming continues to be increasingly profitable and threat actors are likely to continually adapt and improve their techniques.
As E-commerce Threats Rise, POS Malware is in Decline
POS malware planted on physical payment processing devices has enabled threat actors to steal payment card data from terminals at retail stores, hotels, restaurants and other establishments since at least 2008.
Several large-scale POS malware attacks brought this attack type to the headlines particularly in 2014 — including the Target breach that affected 41 million payment card accounts, and signaled the heyday of this attack type.
POS malware remained popular through 2017, but as chip-and-PIN technologies are being used by more card issuers worldwide, the effectiveness of POS malware has been decreasing.
Chip-and-PIN equipped cards — also known as EMV (Europay, MasterCard and Visa, the originators of the technology) — encrypt card data during a transaction, hindering an attacker’s ability to scrape the data from a payment card terminal.
Often, attackers are seeking to steal payment card information to turn around and sell that data on the darknet for a profit. The lower the number of payment cards the attacker can steal, the lower their profit. Ultimately, attackers are finding POS malware not profitable enough to continue these attacks in the same volume as in 2014-2017.
What IBM Data Tells Us: POS Malware Attacks Have Declined Since 2018
Looking at X-Force data from 2020, a continual decline in POS malware is most notable in the retail sector, which has experienced the vast majority of POS malware attacks X-Force has remediated in past years.
In 2018, POS malware attacks in the retail sector made up 13% of all attacks in that industry. In 2019, that percentage shrank to 6%; in 2020, although some attacks were reported globally, our team did not respond to any POS malware attacks on retail organizations.
Figure 2: POS Malware Attacks Against Retail Have Decreased Significantly Since 2018 (Source: X-Force)
Similarly, IBM Managed Security Services (MSS) data gathered from our monitored customers demonstrates a similar trend. Compared to the typical volume of network traffic associated with active malware strains, 2020 showed minuscule detections for POS malware across all sectors.
While X-Force data suggests that POS malware attacks are becoming rare in 2020, other vendors continue to see sporadic attacks. According to one report from Visa, threat actors in May and June 2020, were using various types of POS malware in attempts to harvest payment card data from victimized merchants.
In addition, an X-Force search on VirusTotal for six well-known POS malware families returned around 2,000 samples that have recent detections and have been submitted and compiled on or after Oct. 1, 2020.
Even so, it is unclear how successful contemporary POS malware attacks are. One new strain of POS malware discovered in November was designed to harvest only cardholders’ names, rather than payment card information — suggesting that some POS malware attackers in 2020 are intentionally targeting only personally identifying information, rather than full payment card information.
Regardless of their success, X-Force analysts recognize that POS malware is not gone just yet.
Financially Motivated Actors Exiting the POS Malware Scene
X-Force researchers are following closely several groups who in the past have actively deployed POS malware on merchants across the world. Two such groups in particular — ITG08 and ITG14 — appear to have broadened their attack arsenal, diversifying to other types of cyber crime, and potentially exiting the POS malware scene altogether.
ITG08
An advanced cyber criminal group X-Force tracks as ITG08 has campaign overlap with FIN6 and has been active since at least April 2016. Historically, this group has focused on deploying POS malware — particularly the FrameworkPOS malware — and then stealing payment card data and posting this for sale on the darknet.
However, X-Force and other vendors’ research from 2019 suggests that ITG08 has expanded its operations to include e-commerce card skimmers — online transactions where a credit card is not physically present — and is connected to e-commerce card group Magecart Group 6.
Some security researchers believe ITG08 has been involved in ransomware operations. The group has reportedly been involved in Ryuk and LockerGoga ransomware attacks in 2019. Additionally, X-Force observed a threat actor using tactics and techniques very similar to ITG08 attempt to deploy MegaCortex ransomware 2019.
Therefore, X-Force analysts consider it plausible that ITG08 actors have expanded operations beyond payment card theft to ransomware operations — a segment of the cyber crime market that is becoming increasingly lucrative. The comparative income-generating opportunities from ransomware compared to POS malware may even, conceivably, have prompted ITG08 to exit the POS malware market.
X-Force incident response has not observed ITG08 deploy POS malware since 2018. And, threat intelligence analysts are not aware that any other vendors have observed this group deploying POS malware in 2020, either.
ITG14
A separate advanced cybercriminal group IBM tracks as ITG14 shares campaign overlap with FIN7. This group also has aggressively deployed POS malware on victim networks in the past. According to the U.S. Department of Justice, as of 2018 this group had stolen more than 15 million credit card numbers from over 3,600 businesses in the U.S. alone.
In mid-2020, X-Force researchers were able to identify ITG14 as at least one affiliate group propagating the Sodinokibi ransomware. A 64-bit Carbanak backdoor used in a Sodinokibi ransomware attack observed by X-Force matched a backdoor known to be used by ITG14, and not attributed to any other group.
For this reason, X-Force analysts assess that ITG14 has widened its attack activity to include ransomware attacks. It is possible that ITG14 is devoting more attention to ransomware operations in 2020, given the comparable profitability of Sodinokibi ransomware operations — pulling in over $100 million in 2020 by October alone, according to one interview with a Sodinokibi actor.
While ITG14 would receive only a portion of the ransomware payments for the options in which the group was involved, these profits are still likely to be higher than those associated with POS malware attacks in 2020.
Will POS Malware Decline into Oblivion?
While POS malware is in considerable decline in 2020, it has the potential to rise again if cyber criminals find new ways of circumventing chip-and-PIN technologies.
In July 2020, security blogger Brian Krebs indicated that several U.S. merchants had suffered attacks that sidestepped chip card security controls. The problem associated with chip-and-PIN controls in that case appeared to be a security misconfiguration on the part of the card issuer, where backend systems accepted transactions with information that should have been specific to one transaction only.
Even so, cases of circumventing chip-and-PIN technologies appear to be rare. The profitability of POS malware attacks is declining over time, pushing threat actors out of the POS malware scene and into e-commerce skimming, as well as other more lucrative attack methodologies.
X-Force analysts are reluctant to conclude that POS malware is dead, given the potential for malware innovation. At least for now, prior POS malware actors appear to be focusing more attention on e-commerce payment card theft, ransomware attacks and potentially other attack types.
Shifting Focus to E-commerce Protection, Ransomware Response
As X-Force observes fewer POS malware attacks each year, e-commerce payment card theft attacks are rising in its place. The threat actors who once dominated the POS malware space have now expanded — and probably moved on — to focus on e-commerce attacks and ransomware operations.
This development suggests that retail, restaurant, hotel and other establishments frequently targeted for payment card data will want to focus security on e-commerce threats or even to prepare for ransomware attacks.
X-Force analysts recommend assessing risk from relevant threats, preparing incident response plans for e-commerce and ransomware attacks and rehearsing incident response plans to ensure that teams can respond quickly and effectively if ever an incident is discovered.
Recommendations
- First of all, implement a strategy to prevent unauthorized data theft, especially as it applies to uploading large amounts of data to legitimate cloud storage platforms that attackers can abuse.
- Secondly, go ahead to harden web applications and underlying infrastructure to prevent malicious code injection.
- Thirdly, you need to Encrypt card data in transit and at rest to protect customer data from unauthorized use if it is ever compromised.
- Fourth thing to do is to establish and maintain offline data backups to assist in rapid recovery should data be lost due to a ransomware attack.
- Make use of Employ user behavior analytics to identify potential security incidents.
- Do not forget to employ multifactor authentication on all access points into an enterprise network.
- Next thing to do is to use penetration testing to identify weak points in enterprise networks and vulnerabilities that should be prioritized for patching.
- Lastly, you havr Plan and rehearse incident response procedures for cases of a data breach or ransomware threat.