Mobile edge computing is an emerging technology that provides cloud services and IT services to mobile users within a short distance. Traditional network operators are responsible for controlling the transmission flow (such as forwarding and packet filtering), but in mobile edge computing, cloud servers are also deployed on each base station.
Therefore, network operators have also assumed an important responsibility for providing services to mobile users. The mobile edge computing platform reduces network latency by providing computing and storage capabilities for the edge network. It also enables application developers and content providers to use real-time wireless devices to receive network information to provide context-aware services (such as collaborative computing).
Mobile devices and IoT devices often use mobile edge computing services to perform computational offloading for computationally intensive applications, such as image processing and mobile games.
In this paper, some promising real-time mobile edge computing application scenarios are discussed. Subsequently, the paper showed the most advanced research results in the field of mobile edge computing. The paper also introduces the classification of mobile edge computing and describes the key attributes of mobile edge computing. Finally, the paper clarifies and discusses the challenges that must be faced before the successful deployment of mobile edge computing.
Introduction
Recently, mobile devices (such as mobile phones, smartphones, tablets, etc.) have gradually become important tools for learning, entertainment, participating in social networks, understanding news, and handling business affairs. However, due to the resource limitations of mobile devices (processing power, battery life, storage capacity), the user satisfaction of mobile users is often lower than that of desktop users.
After the development of mobile cloud computing, many cloud computing services such as mobile healthcare, mobile learning, mobile games and mobile management lights can be directly accessed from mobile devices. Because of the need to transmit and receive data between mobile devices and cloud data centers, this also indicates a higher network load and higher network bandwidth requirements. It is estimated that the annual bandwidth demand may increase exponentially.
In addition, the new Internet of Things (IoT) paradigm enables resource-constrained devices to be connected via the Internet. However, many of these edge devices have achieved low processing performance and storage capacity through embedded methods.
In order to overcome the above mentioned problems such as network load/bandwidth limitation in mobile cloud computing or IoT scenarios, some new technologies have been proposed, such as universal access, computing offloading, etc., so that edge devices can offload some computing Tasks to remote resource-rich cloud platforms (such as Amazon EC2 and Window Azure, etc.), thereby saving energy consumption during processing.
However, offloading computing tasks to the public cloud may involve long delays in data exchange between the public cloud and edge devices via the Internet. In order to overcome the above-mentioned problems, a cloudlet-based method for computing offloading is proposed. The mobile device offloads computing tasks to a server that has fewer resources nearby the user, and accesses it through a Wi-Fi access point.
However, compared with cloud computing, Cloudlet has lower computational efficiency. The reasons are as follows: First, Cloudlet can only access nodes via Wi-Fi, and can only cover a small area physically, so it cannot provide computing support that is common everywhere. Second, compared with the cloud, Cloudlet has fewer resources. Therefore, it does not have scalability in terms of services and resource configuration. In order to overcome the above-mentioned challenging problems, a new specification called mobile edge computing has recently been proposed.
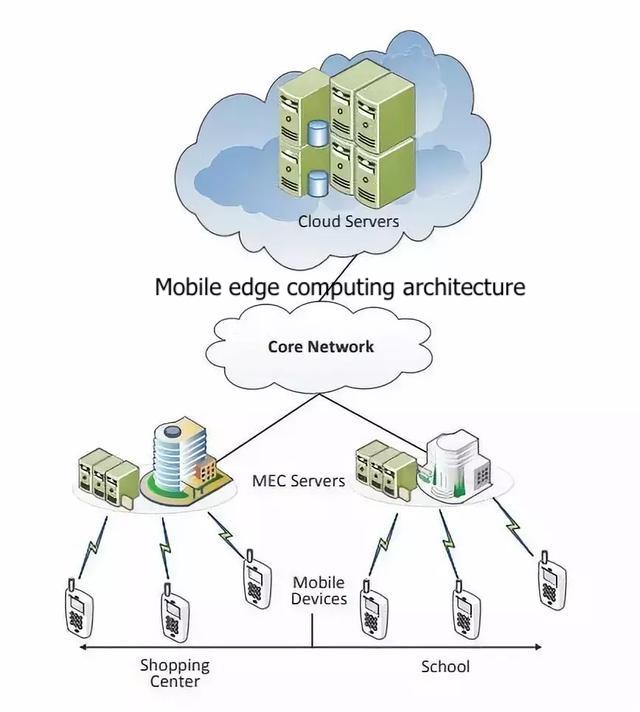
Mobile edge computing enables mobile users to receive services provided by neighboring IT and cloud computing within the wireless communication network (RAN). The main goal of mobile edge computing is to reduce the delay caused by the introduction of computing and storage capabilities from the core WAN to the edge network.
Mobile edge computing can be defined as ” mobile edge computing is a business-oriented cloud computing platform model that provides mobile users with wireless access to nearby networks to accept delay-sensitive, context-aware applications. “
Mobile edge computing provides real-time RAN information (such as network load, user location, etc.) for application developers and content providers. This real-time network information is used to provide context-aware services for mobile users, thereby enriching user satisfaction and improving the quality of user experience (QoE).
The mobile edge computing platform adds responsibilities to the edge network, allowing the edge network to perform computing and service management authority, so as to reduce the network delay and bandwidth consumption of mobile users. Network operators can allow the edge of the wireless communication network to be handled by third-party partners. For mobile users and enterprises, this will allow rapid deployment of new applications and edge services.
Figure 1 shows the novel architecture of mobile edge computing. There are three basic components in the architecture:
- Including all types of edge devices that can be connected to the network (both mobile networks and the Internet of Things);
- The edge cloud is deployed in a cloud with fewer resources on each base station. The edge cloud is responsible for traditional network traffic control (forwarding and filtering, etc.), and management of various mobile edge applications (edge medical, intelligent tracking, etc.);
- The public cloud is the basic cloud architecture deployed on the Internet.
The main goals of mobile edge computing are:
- Optimize mobile resources such as image processing and mobile games by deploying computationally intensive applications on the edge network.
- Optimize big data before sending to the cloud.
- Enable mobile users to enjoy nearby cloud services.
- Provide context-aware services with the help of RAN.
The contributions of this paper are: (a) A survey of the most advanced research results in the field of mobile edge computing. (B) Design classification based on various attributes, such as features, examples, access technologies, applications, goals, computing platforms and key enabling factors, etc. (C) List the various open challenges to be faced in implementing mobile edge computing. The outstanding open challenge bottlenecks will provide direction for researchers in the field.
The structure of this article is as follows:
Part 2 describes some real-life application scenarios, and puts forward potential requirements for mobile edge computing platforms. Part 3 introduces a survey of the latest research results in the field of mobile edge computing. Part 4 shows the classification of mobile edge computing and the different attributes involved in the classification definition. Finally, in Part 5 and Part 6, the open research challenges of mobile edge computing are presented, and a summary of the paper and readers’ evaluation is made.
Motivation
This section introduces the current application scenarios in the field of mobile edge computing to provide motivation for researchers in the field. The mobile edge computing platform is suitable for the following application scenarios, dynamic content optimization, computing offloading in the Internet of Things, mobile big data analysis and intelligent transportation, etc. These applications are not suitable for mobile or portable devices because they are often computationally intensive and require huge storage capacity.
1. Dynamic content optimization
Content optimization is performed on the web host to meet customer expectations. For this purpose, traditional content optimizes the use of user browsing records stored in the database. Sometimes content optimization is also done by asking the user’s current geographic location and analyzing it based on the location information. Content optimization can be done dynamically based on the user’s context-aware information. With mobile edge computing, content optimizers can be deployed on edge servers. In this scenario, the content optimizer obtains accurate cell and RAN dynamic information (network load, network status, etc.) and performs optimization based on the content. The edge network improves performance through content-based optimization, improves user experience quality, and provides new services.
2. Computing Offload in the Internet of Things
Due to the recent exposure of wearable and low-processing power IoT devices, traditional highly computationally intensive device applications (such as augmented reality and surveillance systems) cannot be executed in the device itself. The problem can be solved by dividing IoT applications into small tasks, and some tasks are performed in the cloud (such as the core network) to reduce latency and improve accuracy. The above scenarios can be optimized by offloading tasks on edge servers, without the need to transfer tasks to the core network. Therefore, offloading on the edge server will definitely reduce latency. There are two challenges in computing offloading in mobile edge computing: How to split the IoT application? How to identify whether a task should be uninstalled? How to synchronize the application when the user enters?
3. Mobile big data analysis
In recent years, mobile phones have become the main way to surf the Internet, making mobile devices the most effective way for companies to understand and analyze target markets. Big data is a large amount of structured and unstructured data. Big data analysis is the process of analyzing big data in order to make better strategic business initiatives. In traditional big data analysis, data from edge devices are collected and transferred to the core network for big data analysis. This process puts high demands on bandwidth and latency. In order not to waste a lot of resources in terms of bandwidth, mobile edge computing platforms can be used for big data analysis. Big data analysis can be performed at the edge of the network and the results sent to the core network. Therefore, this scenario will reduce bandwidth consumption and improve network latency.
4. Intelligent transportation
The purpose of intelligent transportation is to solve related key problems such as poor traffic faced by urban residents, such as poor transportation network, poor road conditions, insufficient parking space, insufficient public transportation capacity, and road safety. For example, real-time data collected by edge networks such as cameras and sensor devices installed on the roadside can be used to automatically control traffic. Sensor devices can detect approaching objects (such as pedestrians and vehicles) and can measure the distance and speed of objects. Based on the collected data, the traffic flow can be re-planned through appropriate intelligent traffic light signals for traffic control. Similarly, the smart parking system can use the edge network to model and analyze the available space near the user device by collecting user context information.
Mobile Edge Network: The most advanced research results
The mobile edge computing platform strengthens IT and cloud services at the edge of the wireless communication network through its neighboring edge devices. In this section, we will describe the most advanced research results in the field of mobile edge computing.
1. FemtoClouds
Habak et al. proposed the FemtoClouds system, which provides a dynamically self-configurable “multi-device” mobile cloud system by coordinating multiple mobile devices to expand Cloudlet computing. FemtoClouds uses nearby unused mobile devices to provide a “compute as a service” service at the edge of the network, thus reducing network latency during offloading computing tasks to traditional cloud data centers.
The devices in FemtoClouds can be divided into the following three categories: cloudlet, which can create Wi-Fi access points and act as control devices; computing clusters, which are a group of mobile devices that share hardware and resources; mobile devices, which try to use computing as a service Complete calculation uninstallation.
Initially, the mobile device sends device information (the computing availability of the mobile device, the calculations that can be used for sharing, the available history) and joins the computing cluster through the Wi-Fi network to achieve the purpose of sharing the strategy with the cloudlet. Based on the computing availability and battery level of the device, Cloudlet can refuse to include new devices in the computing cluster.
Mobile devices can offload computationally intensive tasks by sending calculation codes, input and output data sizes to the cloud. Input tasks are prioritized by calculating the required computing time (if available, otherwise use the Mantis system on the available mobile device). The FemtoClouds control uses a greedy heuristic to optimize the scheduling model when the mobile device inputs tasks.
The FemtoClouds system provides community-based computing services by minimizing dependence on enterprise structure and expanding computing capabilities. The performance of computing offloading in the system depends on the number of mobile devices available in the computing cluster and the total amount of hardware resources of unused devices.
2. REPLISOM
Abdelwahab and others proposed REPLISOM, a mobile edge cloud architecture to reduce the number of cloud responses when multiple IoT devices copy memory objects to the edge cloud through the LTE environment. The REPLISOM architecture utilizes cloud computing to enhance the evolved NodeB (eNB) to provide virtual machines for edge resources to perform storage and network resource replication for specific IoT applications.
In REPLISON, the edge cloud pulls the memory copy to a new specific virtual machine copy instead of pushing updated memory objects. In REPLISOM, the LTE-optimized memory replication protocol uses the sparsity in the memory to infer the number of communications.
When multiple IoT devices (assuming there are multiple devices, a total of n devices) try to update the memory object, each device uses the communication technology between the devices to send the updated memory object update to neighboring devices instead of sending them to the edge cloud. The receiving device (assuming the jth) compresses the receiving memory copy into one copy.
The edge cloud periodically sends pull requests (using pre-arranged uplink authorization) to the corresponding IoT devices. When device J receives a pull request from the edge cloud, it pushes the compressed copy to the edge cloud in response. Finally, the edge cloud uses a compressed sampling construction algorithm to restore the memory objects and store them in the corresponding virtual machine.
The REPLISOM architecture updates objects to the nearby edge cloud when multiple IoT devices are replicated during unloading to reduce latency and costs.
3. ME-VOLTE
Baker et al. proposed mobile edge computing to implement Voice over LTE (ME-VoLTE) architecture to reduce battery consumption during video calls on mobile devices and provide a communication protocol for negotiating offloading strategies. The video encoding process during the video call is offloaded on the MEC edge server.
VoLTE is based on an IP multimedia system. There are two main components in the VoLTE architecture: 1. Proxy/service call state control function or (P- / S-CSCF), its task is to send mobile equipment (UE) and VoLTE network signal. 2. The media resource function (MRF) is a part of the VoLTE network, responsible for media mixing, storage media playback, and media transcoding.
Called when the mobile device tries to make a video, the request (and the set of codec names) is sent to the MRF by using a proxy (P/S-CSCF). MRF is based on the currently available calculated coding type resources and uplink strength negotiation. After the negotiation, the mobile device encodes the video (sent by P/S-CSCF) by selecting one of the codecs and sends the media to ME-MRF. The VoLTE protocol uses a session initiation process during a video call.
ME-VoLTE is a video-based mobile edge computing phone system to reduce energy consumption in video calls.
4. Multi-user computing offload
Chen et al. proposed an offloading model of distributed computing tasks for mobile edge computing. This model uses competition theory to obtain the Nash equilibrium when multi-users are performing computing tasks offloading. When multiple devices use the same wireless channel to offload the computing task to the telecom cloud at the same time, the time will be calculated first, and the task will be offloaded to the cloud when the time is shortened and the energy consumption is reduced after the computing uninstallation.
The author standardized the offloading decision-making problem, and transformed the multi-channel wireless environment involving multiple users into a multi-user computing task offloading competition. In a multi-user competition, whether to uninstall or not depends on the performance of all cloud resource users. Here, if the Nash equilibrium is not violated, the device can choose to offload the task to the cloud.
The advantage of the above model is that the model can solve the NP-hard problem of multi-user computing task offloading.
5. Computing offloading between mobile device clusters
Gao et al. proposed a probability-based computing task offloading framework, which is applied to computing offloading between mobile device clusters under the same strategic level. In the war zone, some applications, such as processing live perception data of nearby environments, require a lot of calculations.
The framework offloads some applications to nearby mobile nodes to reduce computing time and energy consumption. Whether a node is offloaded or not depends on its computing power, the energy and activity levels of neighboring nodes, and the possible future connections between them. Two nodes can predict their future connection through application attributes such as the distribution of contact time (ICT) between mobile nodes.
According to the proposed framework, before unloading, the mobile node calculates the computing time, energy consumption and future connections of the task at the new node. If time and energy consumption are reduced, and the new node ensures that the task can be completed within the task deadline, the new node unloads the task. If task offloading has the opportunity to use the above technique, the task is recursively offloaded at nearby nodes.
The proposed model recursively assigns the tasks of a mobile node (at the tactical edge) to its neighboring nodes. This model reduces energy consumption and improves task throughput. The performance of the above model depends on the number of adjacent nodes in the edge network. If a node suddenly leaves the network, the model does not consider its involvement.
6. Continuous convex approximation algorithm framework for computing task offloading
Sardellitti et al. proposed the Continuous Convex Approximation Algorithm Framework (SCA) for the optimization of wireless communication and computing resources when computing tasks are offloaded in multi-unit mobile edge computing scenarios. The optimization problem is defined as the joint optimization of mobile users’ wireless communication and computing resources, by minimizing the energy consumption and delay period of mobile devices under budget power.
In the framework, the edge network has multiple cell enhanced Node Bs (SCeNB), which are linked to the public cloud server provider for offloading purposes. Mobile users in the same unit use orthogonal channels for cloud communication. Therefore, this framework is also suitable for dense computing units. Mobile multi-user access to different units may interfere with each other.
Considering that the cloud server provides computing resources and the battery power of the device, mobile users can offload computing tasks in the remote cloud or execute them locally. The author proposes that the above offloading environment is suitable for a single user, and only one mobile user is accessing cloud resources.
In a single user instance, the optimization problem is non-convex, but the author changes the closed-form global optimal solution problem to a convex optimization problem by constructing an algorithm. When cloud resources are accessed by multiple users in a dense cell environment, centralized and distributed SCA-based algorithms obtain the optimal solution to the non-convex optimization problem. Compared with the non-orthogonal optimization algorithm, this algorithm shows better results, and the framework only needs to consider the static values used to perform resource optimization.
7. Edge accelerated Web browsing (EAB) prototype
Takahashi and others introduced the Edge Accelerated Web Browsing (EAB) mobile edge computing prototype to accelerate the execution of network applications. In EAB, edge servers are deployed between mobile clients and neighboring servers. When a mobile web browser sends a URL page request, the server’s response is first intercepted at the edge. In response, the edge server excluded some content. Common tasks of edge servers are to obtain web content, evaluate web content, the layout of content components, and task rendering. The EAB mobile edge computing prototype is better than normal web browsing.
8. Collaborative context-aware real-time applications
Nunna et al. proposed a mobile edge computing architecture based on 5G technology for collaborative context-aware real-world applications. Collaboration applications at critical moments are disadvantageous due to the high latency of wireless communication. In the above architecture, the MEC server is deployed in the eNodeB of each architecture.
The author uses 5G technology, proximity services and the characteristics of context-aware computing to achieve collaboration. The middleware MEC collaboration platform in the MEC server collects important information through standard APIs, such as user fines, granular location, wireless communication level, etc. (expected in 5G). The above architecture will benefit from road accident scenarios and remote robotic remote surgery scenarios.
The above model is low-latency (because of 5G) and is suitable for collaborative computing, such as delay and synchronization are important factors in the performance of the collaborative computing model. Although the concept of 5G technology is still in a state of development, the above model is theoretical.
9. CloudAware
Gabriel et al. proposed CloudAware, a programming model based on mobile edge computing to develop scalable mobile edge computing applications. CloudAware uses the properties of the Jadex middleware framework such as distributed, concurrent execution and context-aware computing.
In CloudAware, Discovery Service is responsible for monitoring the available network, network strength, the uninstallation and workload of each server’s available proxy computing resources. Context Manager collects user mobility status to evaluate the future connection status of the network. Based on the runtime optimization problem (that is, minimizing the calculation time) and the state of the network connection, the partitioner and solver divide the application into different components and develop an uninstall strategy.
The CloudAware framework is an abstract, transparent, and contextual programming model. The framework has not been implemented/simulated, and the performance and reliability of the model cannot be known.
Classification
This section describes the classification of mobile edge computing and a brief description of each component. Figure 2 shows the classification of mobile edge computing. The classification of mobile edge computing is based on the following parameters: a) features, b) actors, c) access technology, d) applications, e) goals, f) computing platforms, and g) key enabling factors.
A. Features
Mobile edge computing can be classified in the following ways:
1) Proximity : In mobile edge computing, the edge network is accessed by mobile devices using RAN. Mobile or portable devices can also access edge servers located in mobile base stations through inter-device (D2D) communication. Because the edge server is near the device, it can extract device information and analyze user behavior to improve services.
2) Dense geographic distribution : Mobile edge computing places host IT and cloud computing services on edge networks located in many places. Geographically dense and dispersed infrastructure has many advantages. Based on user mobility, services can be provided without traversing the entire wide area network.
3) Low latency : One of the goals of mobile edge computing is to reduce the latency of access to the core cloud. In mobile edge computing, applications are deployed on a mobile edge server located on the edge network or the cloud on the edge network. Compared with the core network, the edge network has a high available bandwidth, which reduces the average network delay.
4) Location awareness : Because the mobile device is located near the edge network, the base station collects the user’s movement pattern and predicts the future network state. Application developers use user location to provide contextual services to users.
5) Network environment information : Real-time RAN information (such as user location, wireless communication conditions, network load, etc.) is used to provide mobile users with context-aware services. Application developers and content providers use RAN information to serve service providers, thereby improving user satisfaction and quality of experience (QoE).
B. Actor
The mobile edge computing environment includes many individuals and organizations, and each individual plays a different role to build a platform that provides context awareness, low latency, and on-demand cloud services within the RAN. The overall goal of mobile edge computing is to bring a sustainable business model to all participants and promote the growth of the global market. Actors include application developers, content providers, mobile users, mobile edge service providers, software vendors and over-the-top content (OTT) players.
C. Application
Mobile edge computing provides a series of applications with great potential. Recently, applications in the field of mobile edge computing can be categorized as computing offloading, collaborative computing, memory replication and content delivery in the Internet of Things. These applications use high bandwidth to perform calculations at the edge network, thereby improving network latency. The above applications use network context information to improve user satisfaction by providing different services to users in a mobile state.
1) Computing offload : Many mobile applications are computationally intensive, such as face recognition, voice processing programs, mobile games, etc. However, running computationally intensive applications on resource-constrained devices consumes a lot of resources and power. Transfer part of the computing task to the cloud data platform and return the program execution result after the task is successfully completed, instead of all running in the mobile host. Because the communication between edge devices and the core cloud takes a long time, in mobile edge computing, servers with fewer resources are deployed at the edge of the network. Thus, the purpose of offloading computationally intensive tasks is achieved.
2) Collaborative computing : Collaborative computing enables many individuals and organizations to collaborate in a distributed system. In the current scenario, the collaborative application ranges from simple sensors to robotic remote surgery. In this type of application, the location of the device and communication delay become key elements in communication. Add real-time collaborative applications in the mobile edge environment to provide context-aware collaboration systems.
3) Memory replication in the Internet of Things : In recent years, LTE has become the mainstream connection technology for devices. The computing and storage capabilities of IoT devices are poor. These devices collect data from surrounding and offloaded tasks, and use them as memory objects in a scalable cloud infrastructure for further calculations. As a result, the number of IoT devices continues to grow, and network bottlenecks are caused by the high latency of copying memory objects. The edge network in mobile edge computing creates multiple replicated clouds for each device, bringing the computing power close to the IoT devices and reducing network latency.
4) Content delivery : Content delivery technology optimizes and adjusts Web content on the Web server to provide services with high availability, high performance and reduced delay. Traditional Web content delivery cannot be adjusted according to user requests after optimization. Mobile edge computing can provide dynamic web content optimization based on network status and available network load. Because the devices are very close, edge servers can take advantage of user mobility and service experience to provide content optimization.
D. Access technology
In the mobile edge computing environment, mobile or portable devices communicate with other devices or edge networks through the use of wireless networks, such as cellular networks (GPRS / CDMA / 3G / 4G / Wi-MAX) or Wi-Fi entry points. Because the network is densely deployed, users can connect to the edge network by switching to any available access network.
E. Objective
The objective attribute defines the main goal of mobile edge computing. Each component of mobile edge computing, such as mobile nodes or network operators, has different goals. The underlying structure of mobile nodes using the computing and storage capabilities of mobile edge computing attempts to minimize the computing delay and energy consumption of mobile devices. The goal of the network provider is to minimize the cost of the underlying architecture and increase throughput.
F. Computing platform
The computing platform attribute represents the type of computing performed in the mobile edge computing platform. In peer-to-peer computing, tasks are offloaded to nearby mobile devices. Tasks can be offloaded to nearby clouds deployed on edge networks. In mobile edge computing, mobile edge services are deployed on each base station.
G. Key enabling factors
The implementation of mobile edge computing technology in actual application scenarios is supported by various key technologies. The key enabling factors indicate that different technologies provide context-aware, low-latency, high-bandwidth services for mobile users accessing wireless communication networks.
1) Cloud and virtualization : Virtualization allows different logical structures to be created on the same physical hard disk. The cloud computing platform at the edge of the network uses virtual technology to create different virtual machines to provide different cloud services including Software-as-a-Service (SaaS), Platform-as-aService (PaaS) and Infrastructure-as-a-Service (IaaS) .
2) High-capacity servers : Traditional high-capacity servers or mobile edge servers are deployed in each mobile base station in the edge network. The mobile edge server performs traditional network traffic forwarding and filtering, and is also responsible for offloading tasks.
3) Network technology : Multiple small units are deployed in the mobile edge computing environment. Wi-Fi and cellular networks are the main network technologies used to connect mobile devices with edge servers.
4) Mobile devices : low-computing tasks for portable devices in edge networks and tasks related to hardware that cannot be offloaded to edge networks Portable devices can also perform peer-to-peer computing through communication between edge network devices.
5) Software development kit : The software development kit (SDK) and standard application programming interface (API) help to adjust existing services and accelerate the development of new flexible edge applications for existing services. These standard APIs can be easily integrated into the application development process.
Openness challenge
Mobile edge computing is still in its infancy. There are many challenges to overcome in this area. In this section, we identified some open research challenges in the field of mobile edge computing. Each unsolved problem will give a little idea to solve the problem.
A. Standard Agreement
Standardization brings an open environment for researchers and the industry, enabling work on a unified platform. Mobile edge computing is the latest technology that has not yet been implemented. Therefore, a standardized open environment needs to be created for mobile edge computing, which will allow the mobile edge computing platform to integrate seamlessly and skillfully with traditional applications.
The standard platform will also accelerate the development of mobile edge applications across the industry and ultimately increase the market size. Standard protocols need to implement standard features of mobile edge computing, such as context-aware information, offloading scenarios, etc. Once the standard protocol is available, researchers and experts can improve the protocol after implementation or modeling in a real platform.
B. Simulation platform
The simulation platform is a process of modeling the real world using mathematical formulas, and can be implemented using general programming languages. The model should be able to reconfigure and experiment with different scenarios. The advantage of using simulation is that it can help us understand the entire system and its feasibility (low cost) without an actual implementation model.
Developing mobile edge computing infrastructure and testing requires a lot of effort and financial investment. Developing a simulation platform for mobile edge computing will encourage researchers to experiment with various scenarios of mobile edge computing.
C. Flow management
In the mobile edge computing platform, mobility is one of the reasons for the frequent disconnection of the link between the device and the edge network. When the device is in a mobile state, the service quality of the application is reduced due to changes in network parameters, such as delay, bandwidth, jitter, etc. Implementing mobility management technology is a challenging problem in the mobile edge. Users can access edge applications without any link. Mobile management technology should focus on both horizontal and vertical mobility.
D. Heterogeneity
The edge network in mobile edge computing is highly heterogeneous, which makes sense in terms of wireless network interfaces. Edge devices can access and access services through different wireless communication networks, such as Wi-Fi, 3G, 4G, WiMAX and 5G technologies. Due to the high probability of signal interference in wireless networks, how to manage network handover is one of the challenging issues without adjusting the priority of the basic attributes of mobile edge computing (ie, low latency, high bandwidth and user location awareness) .
E. Pricing model
In mobile edge computing, user mobility is common in places where the network is heterogeneous. If users access edge services from a roaming base station, an appropriate pricing model should be established. The pricing model should be dynamic, based on the network parameters of the access technology
For example, delay, session reconstruction delay, jitter, bandwidth, availability and security, etc.
F. Scalability
Scalability attributes ensure service availability regardless of the number of client devices in the edge network. Under normal circumstances, most devices do not apply for access to the edge at the same time. In recent years, the number of edge devices (such as mobile devices, IoT devices, etc.) has increased. If a large number of devices access services at the same time, this will involve network bottlenecks, and eventually services may be interrupted. Edge servers should ensure service scalability by applying load balancing mechanisms to server clusters.
G. Security
Security is a challenging issue in mobile edge computing, and applications are deployed on the computing platform of the edge network. Compared with traditional computing, the rules made by wireless communication networks make application developers have no role in challenging security policies. Before an application can be deployed on a mobile edge server, the following security challenges must be addressed. The application deployed on the edge server should verify that the user accessing the application’s resources is what it claims to be. Mobile edge servers must protect applications and data stored on the edge servers to avoid intrusion. On the other hand, mobile devices need to verify that the edge application is accessed from the edge server. Finally, the mobile edge computing platform must ensure data integrity.
Latest
- The Security of Cloud API and the Problems to be Solved
- 10 Interview Questions on Kubernetes for SDET/Devops Set-03 (ReplicaSet in K8S)
- 5 Basic Principles for Successful Big Data Analysis Projects
- Cloud Storage: Definition and Meaning?
- How do I Reduce Mobile App Development Cost: Tips
- Don’t Interpret “Big Data & AI” as a “Big Myth”
- IoT in Workplace – Future Smart Office Tech Solutions
- Cloud Computing: The Heart of Global Informatization
- How to Implement Big Data Projects on the Cloud
- Internet of Things (IoT) – How Will it Change the World?
- Top 10 Technology Industry Trends in 2021
Conclusion
Mobile edge computing brings computing and storage capabilities to traditional core networks by accessing wireless communication networks. In this new architecture, traditional base stations can not only perform flow control, but also deploy edge servers/clouds with fewer resources to nearby mobile users to provide context-aware services. The main goal of mobile edge computing is to provide applications and services with less latency and minimal bandwidth.
This paper studies real-time application scenarios suitable for mobile edge computing platforms. Then, the most advanced research results in the field of mobile edge computing are elaborated. Based on our investigation, a classification method for mobile edge computing is proposed and each attribute is clearly described. Finally, the main open research challenges for the successful deployment of mobile edge computing are listed.